For instance, a company may have a strong firewall but weak employee logins, or robust passwords, while sensitive data remains unprotected in applications. Breaches usually arise from multiple minor oversights rather than a single major failure.
This understanding has led to the concept of defense in depth, which emphasizes multiple protective layers across networks, devices, users, applications, and data. This approach allows each layer to act as a barrier and a checkpoint, ensuring that if one fails, another can restrict access or detect suspicious activity.
For businesses in cloud environments, remote work, or public networks, this layered strategy is vital for resilience against evolving threats.
What Is Defence in Depth?
Defence in depth is a cybersecurity strategy that uses multiple security controls across an environment rather than relying on a single one. If one control fails, others are in place to limit access or detect threats, helping prevent a full breach.
Today’s cyber threats often exploit multiple weaknesses. Attackers might start with phishing to steal credentials, then move through the network. Using multiple security layers with defence-in-depth can break this chain.
This method uses network controls to manage traffic, authentication policies to limit access, encryption to protect data, endpoint security for devices, and ongoing monitoring to detect unusual activity. Together, these steps build strong security.
The idea comes from military defense, where several layers protect important assets. Now, defence in depth is a key part of security for businesses, cloud systems, and remote teams. It helps keep systems safe even if one layer is breached.
How the Defense in Depth Model Strategy Works
Defense in depth works by placing security checkpoints at every stage where users, devices, or data interact with a system. Instead of relying on a single protective control, the strategy ensures that access, movement, and activity are continuously verified.
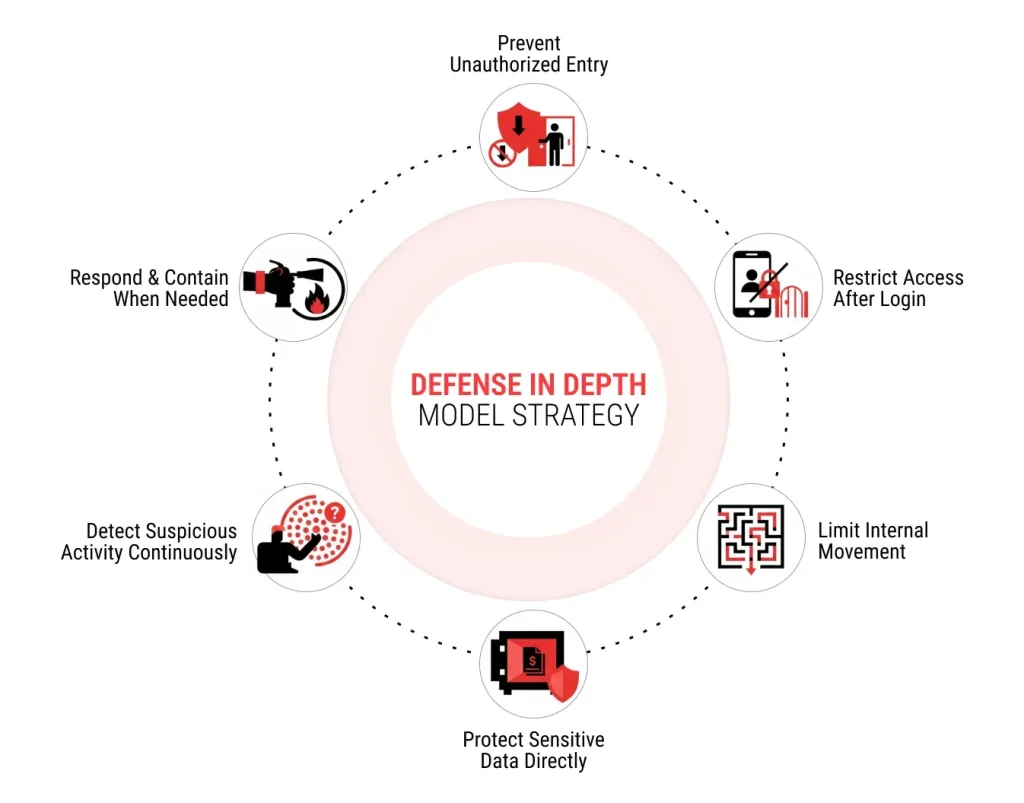
1. Prevent Unauthorized Entry
The first step focuses on reducing the likelihood of attackers entering the environment. This includes network filtering, secure authentication, encrypted connections, and exposure control for public-facing services. These measures address the majority of automated scanning, brute-force attempts, and casual intrusion attempts.
2. Restrict Access After Login
Even when a user successfully signs in, access should not be unlimited. Permission controls define what systems, applications, and data each account can access. This prevents a stolen credential or compromised account from automatically exposing the entire network.
3. Limit Internal Movement
If an attacker gains access to one system, the next layer of protection prevents unrestricted movement within the environment. Network segmentation, device isolation, and service level restrictions ensure that reaching one machine does not provide a pathway to others.
4. Protect Sensitive Data Directly
Defense in depth also assumes that attackers may eventually reach valuable information. Encryption, secure storage policies, and controlled data access reduce the risk of exposure even if infrastructure controls are bypassed.
5. Detect Suspicious Activity Continuously
Preventive measures alone are never enough. Logging systems, traffic analysis, and behavioral monitoring run constantly to identify unusual login patterns, unexpected data transfers, or privilege escalation attempts. Early detection allows security teams to respond before damage spreads.
6. Respond and Contain When Needed
The final part of the model focuses on limiting the impact once a threat is identified. Automated alerts, account lockdowns, session termination, and incident response procedures help contain the attack quickly and prevent further escalation.
Layered Security vs Single Layer Security
Security failures often happen not because protection was missing, but because it existed in only one place. Understanding the difference between single-layer security and layered security explains why modern cybersecurity relies on the defense-in-depth approach.
Single Layer Security
Single-layer security means protection depends heavily on one primary control. This could be a firewall protecting the network boundary, a password protecting user accounts, or antivirus software running on endpoints. If that control works, the system remains protected. If it fails, there is little to prevent further access.
For example, if an attacker steals valid login credentials and the system relies only on password authentication, the attacker can sign in without resistance. Similarly, if a network relies solely on perimeter filtering but internal systems are fully exposed once inside, a single breach can result in unrestricted movement.
This model assumes the first barrier will always hold, which rarely matches real-world attack patterns.
Layered Security
Layered security distributes protection across multiple checkpoints so that no single failure results in full exposure. Entry controls attempt to block unauthorized access, authentication layers verify identity beyond just passwords, network segmentation limits internal reach, and monitoring systems track abnormal behavior throughout the session.
Using the same credential theft example, layered security would require additional authentication before login, restrict what the account can access after sign-in, and generate alerts if activity suddenly deviates from normal usage. Each layer reduces the attacker’s progress even if one safeguard is bypassed.
Layers of Defense in Depth
The layers of defense in depth represent different points where security controls protect systems, users, and data. Instead of relying on one protective barrier, the model distributes safeguards across infrastructure, devices, applications, and access pathways so that a failure in one area does not expose everything.
Each layer addresses a different type of risk, and together they create a structured security environment where access is continuously restricted, verified, and monitored.
- Physical Security Layer
Physical protection forms the outer foundation of any secure environment. If unauthorized individuals can access servers, networking hardware, or employee devices directly, digital controls become far less effective.
This layer includes secured office facilities, controlled data center access, device locking policies, and surveillance measures. Even in cloud-based environments, physical protection remains relevant because endpoint devices such as laptops and mobile phones still store credentials and access tokens.
- Network Security Layer
The network layer regulates how systems communicate and which connections are allowed. Firewalls, intrusion detection systems, traffic filtering, and network segmentation help prevent unauthorized access and reduce exposure to external threats.
Secure, encrypted connections also play an important role here. When users connect through unprotected public networks, their traffic can be intercepted or manipulated. Encrypted VPN tunnels ensure that communication between the user and the destination remains protected, preventing attackers from exploiting exposed network traffic as an entry point.
- Endpoint Security Layer
Endpoints such as laptops, desktops, and mobile devices are often the first practical targets for attackers. If a device becomes compromised, it can be used to steal credentials, install malware, or access internal systems.
Endpoint protection focuses on system updates, malware detection, device hardening, and controlled software permissions. Keeping endpoints secure reduces the chances that attackers gain a reliable foothold inside the environment.
- Application Security Layer
Applications frequently handle authentication, business logic, and sensitive data processing. Vulnerabilities in web applications, APIs, or internal software can allow attackers to bypass other controls entirely.
Application security includes secure development practices, regular vulnerability testing, patch management, and input validation. Protecting this layer prevents attackers from simply exploiting the software to gain unauthorized privileges.
- Data Security Layer
Ultimately, most attacks target data rather than infrastructure. The data layer ensures that sensitive information remains protected even if other controls are bypassed.
Encryption during storage and transmission, strict access permissions, and secure backup policies all contribute to protecting information directly. If attackers cannot read or extract the data they reach, the impact of a breach is significantly reduced.
- Identity and Access Management Layer
Identity control decides who can access systems and what actions they can take. Poor identity management often leads to major security breaches.
Strong authentication, multi-factor authentication, session monitoring, and role-based permissions help ensure users do not exceed their authorized access. These steps stop stolen credentials from giving someone full control of a system.
- Monitoring and Response Layer
No security architecture is complete without continuous visibility and response capability. Logging systems, behavioral monitoring, anomaly detection, and incident response procedures help quickly identify suspicious activity.
Even if attackers bypass preventive layers, monitoring ensures their actions are detected and contained before widespread damage occurs. This final layer turns defense-in-depth from passive protection into an active security posture.
Defense in Depth vs Zero Trust Security
Defense in depth and Zero Trust security are often mentioned together, but they solve different parts of the same problem. One focuses on building multiple protection layers across systems, while the other verifies every access request, regardless of location or prior authentication.
| Aspect | Defense in Depth | Zero Trust Security |
|---|---|---|
| Core Idea | Multiple layers of protection across systems | Continuous verification for every access request |
| Primary Focus | Infrastructure protection and risk reduction | Identity validation and access control |
| Security Approach | Build several defensive checkpoints | Never trust any user or device automatically |
| Trust Model | Some trust may exist after authentication but is restricted by layers | No implicit trust at any stage of access |
| Protection Scope | Network, endpoints, applications, data, monitoring | Users, devices, sessions, and permissions |
| Goal | Prevent a single failure from causing full compromise | Ensure every action is verified before allowing access |
| Relationship to Each Other | Provides the structural security framework | Acts as an enforcement method within that framework |
How Integrated Security Strengthens Defense in Depth
Defense in depth relies on multiple protection layers, but those layers work best when they share signals and react together. If security tools operate in isolation, attackers can exploit the gaps between them. Integrated security connects detection, alerts, and enforcement so that the entire system responds as one.
Eliminates Blind Spots Between Security Layers
When controls are disconnected, one system may detect a threat while another still allows access. Integrated security ensures that once a device, session, or user is flagged as risky, other controls adjust immediately to reduce exposure.
Speeds Up Threat Detection and Response
During an intrusion, a delayed response gives attackers time to escalate privileges or move deeper into the network. Shared logging and coordinated alerts enable authentication systems, network controls, and monitoring tools to respond together and restrict suspicious activity more quickly.
Strengthens Identity and Access Enforcement
Integrated security evaluates access using multiple signals at once, including credentials, device status, location patterns, and recent behavior. If any indicator raises risk, permissions can be tightened automatically, preventing attackers from exploiting isolated approval points.
Supports Consistent Protection Across Remote Networks
Users now connect from home networks, mobile devices, and public connections. Integrated security ensures that encrypted access, authentication checks, and traffic monitoring are applied consistently regardless of the connection’s origin.
Turns Defense in Depth Into a Coordinated System
Layered protection creates multiple barriers, but integration reinforces them. When systems share intelligence, suspicious activity detected at one layer strengthens protection at others, making the entire architecture harder to bypass.
Common Mistakes When Implementing Defense in Depth Strategy
Many organizations adopt layered security tools but still remain vulnerable because the implementation focuses on quantity rather than placement and coordination.
Treating More Tools as Better Security
Simply adding more security products does not guarantee defense-in-depth. If the controls overlap but do not address different stages of an attack, there will still be gaps. This approach is effective only when each layer protects a specific area, like entry, movement, access, or data exposure.
Ignoring Internal Movement Risks
Some environments focus heavily on blocking external threats while leaving internal systems broadly accessible once a user signs in. If a credential is stolen, attackers can move freely. Proper layered security must also restrict activity after authentication.
Weak Identity Controls
Stolen credentials remain one of the most common entry points for breaches. Relying only on passwords or static access permissions undermines the entire model. Strong authentication checks and limited privilege access are essential for preventing small compromises from becoming major incidents.
Lack of Continuous Monitoring
Preventive controls alone cannot stop every threat. Without logging, anomaly detection, and response mechanisms, suspicious behavior may continue unnoticed even when multiple security layers exist.
How Organizations Can Build a Practical Layered Security Architecture
Building defense in depth does not require complex enterprise infrastructure. It requires placing the right safeguards at the right operational stages.
Identify Critical Systems and Data
Start by mapping which systems store sensitive data, control business operations, or manage user access. These areas should receive the strongest layered protection.
Control Entry Points
Secure login pathways, external services, and network access channels first. Strong authentication requirements, encrypted connections, and controlled exposure reduce the chances of unauthorized entry.
Restrict What Happens After Login
Users and services should only access what they genuinely need. Role based permissions and segmentation prevent a single compromised account from exposing the entire environment.
Protect Devices and Applications
Ensure endpoints remain updated, restrict unsafe software behavior, and regularly patch applications. Many successful breaches begin from outdated systems or compromised devices.
Monitor Activity Continuously
Track login patterns, data transfers, privilege changes, and unusual traffic behavior. Early detection allows organizations to respond before attackers gain deeper control.
Defense in Depth for Remote Work and Public Networks
With remote work, people no longer connect from a single secure office network. Instead, they use home WiFi, cafés, hotels, airports, and shared workspaces. These places often lack strong security, so attackers can easily monitor traffic, intercept sessions, or set up fake hotspots to trick users. That’s why using multiple layers of defense is so important.
Public WiFi Increases Risk
You should always consider public networks unsafe. Attackers might watch open traffic, intercept data, or steal login details from weak connections. Even if a website uses encryption, attackers can still learn things like DNS requests or connection habits.
Since people often change networks, you should not depend only on the security of your current connection.
Encrypted VPN Tunnels Protect Data in Transit
A VPN sets up a secure, encrypted connection between your device and the internet. This keeps your data safe before it reaches any public network. If someone tries to watch your activity on local WiFi, all they see is scrambled data, not your sessions, passwords, or browsing history.
With layered security, a VPN protects your connection, not just your account or the apps you use.
Secure DNS Helps Prevent Redirection and Tracking
DNS requests decide which servers a user connects to. If these requests are exposed, attackers may track browsing activity or attempt to redirect users to malicious sites. Secure DNS handling ensures these lookups are protected, so traffic reaches the correct destination without interference.
This adds another protective layer working alongside encrypted traffic.
IP Masking Reduces Direct Exposure
Connecting directly to a public network exposes the user’s real IP address, which can reveal their location and attract targeted scanning attempts. Routing traffic through a secure network hides the real address and limits how much information outsiders can gather about the user or their connection.
Real World Example of Defense in Depth
Recent cyber incidents show that attackers rarely rely on a single sophisticated exploit. Most successful breaches begin with a simple entry method and expand because additional security layers fail to restrict access, movement, or detection.
Microsoft Corporate Email Breach, January 2024
In January 2024, Microsoft disclosed that a Russian state-linked group known as Midnight Blizzard accessed corporate email accounts belonging to senior leadership and security personnel. The attackers initially gained entry in late November 2023 through a password-spraying attack against a legacy test tenant that lacked strong authentication controls.
Once access was obtained, the attackers used the account’s permissions to gain access to internal systems and extract emails over several weeks before detection.
From a defense-in-depth perspective, the initial password spray should not have resulted in prolonged internal access. Stronger enforcement of multi-factor authentication across all tenants, removal of legacy authentication pathways, and tighter monitoring of unusual mailbox access patterns could have introduced additional barriers. The breach demonstrated how even large organizations can be exposed when older identity pathways remain active without layered safeguards.
Snowflake Customer Data Breaches, May to June 2024
During mid-2024, multiple companies reported data theft linked to compromised Snowflake cloud data accounts. Attackers used previously stolen credentials from unrelated breaches to log in to Snowflake environments that did not require mandatory multi-factor authentication.
Because the logins appeared technically valid, attackers were able to access stored datasets and extract large volumes of customer information from affected organizations.
This incident highlights a classic layered security failure. Credential theft alone should not provide direct access to sensitive data storage. Mandatory secondary authentication, behavioral login analysis, tighter role permissions, and outbound data transfer monitoring could have limited or detected the activity much earlier. The breach showed how cloud infrastructure remains highly vulnerable when identity protection is treated as a single checkpoint.
Change Healthcare Ransomware Attack, February 2024
In February 2024, UnitedHealth’s Change Healthcare division suffered a major ransomware attack that disrupted pharmacy processing, insurance claims, and healthcare payment systems across the United States. Reports later indicated that attackers gained access by using stolen credentials for a remote access system.
After entering the network, ransomware deployment forced systems nationwide offline and caused widespread disruption to healthcare services, lasting weeks.
This case shows how a single compromised remote access credential can escalate into large-scale operational failure when additional safeguards, such as enforced multi-factor authentication, strict privilege segmentation, and aggressive internal activity monitoring, are insufficient. Defense in depth exists specifically to prevent remote access credentials from becoming a direct path to infrastructure-level control.
Conclusion
Modern cybersecurity is no longer about building a single strong barrier and hoping it holds. Attackers today use layered methods, automated tools, and stolen credentials to test systems from multiple angles. In this environment, protection has to exist at multiple points as well.
Defense in depth provides that structure. By combining network safeguards, strong identity controls, device protection, encrypted connections, and continuous monitoring, organizations reduce the risk that any single mistake becomes a serious breach. Even when attackers succeed at the first step, additional layers limit how far they can move and how much damage they can cause.
For remote teams, cloud environments, and users connecting through public networks, this layered approach becomes even more important. Security is no longer tied to a single office perimeter. It must travel with the user, protect the connection, and continuously verify access.
The goal of defense in depth is not to promise perfect security. It is to make successful attacks far more difficult, far more visible, and far easier to contain.
FAQs
What is the difference between layered security and integrated security?
Layered security means placing multiple protections at different points in a system so that one failure does not expose everything. Integrated security means those protections share information and respond together. In simple terms, layered security adds multiple defenses, while integrated security makes those defenses work as a coordinated system.
How does defense in depth relate to Zero Trust security?
Defense in depth is the overall strategy of using multiple security layers across infrastructure, users, and data. Zero Trust is an access model that requires every user and device to be verified continuously. Zero Trust typically serves as one enforcement approach within a broader defense-in-depth architecture.
How does multi-factor authentication strengthen defense in depth?
Multi-factor authentication adds another verification step beyond a password, such as a code or device approval. This prevents stolen credentials from immediately granting access and creates an additional barrier within the layered security model.
Can defense-in-depth prevent all cyberattacks?
No security model can stop every attack. Defense in depth is designed to reduce the chances of success and limit the damage if an attacker gets in. Forcing attackers to bypass multiple controls makes breaches far harder to execute and contain.
Table of Contents
