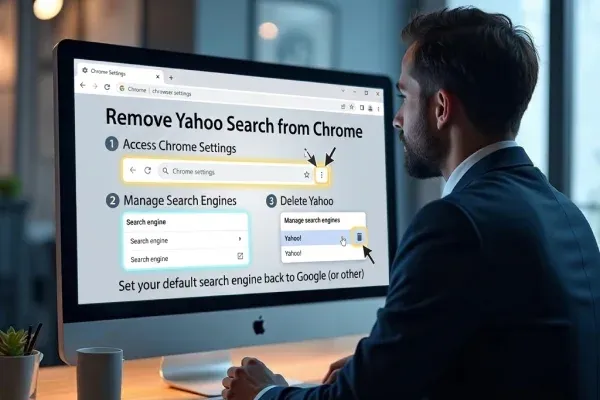
How to Remove Yahoo Search from Chrome
You didn’t change anything. You didn’t ask for this. And yet, here it is, redirecting you every single time. This isn’t a glitch, and it’s not something Chrome did on its own. If Yahoo Search has quietly taken over your browser, there’s a very real chance your system has been compromised by a browser hijacker. The good news is that
What Is Defense in Depth? How It Protects Modern Systems
For instance, a company may have a strong firewall but weak employee logins, or robust passwords, while sensitive data remains
Arsalan Rathore – Updated 02/20/2026
What Is a Botnet? Understanding Botnet Attacks and DDOS threats
Introduction Botnets quietly infect thousands or even millions of devices, turning them into remote-controlled weapons that can launch devastating attacks.
Bisma Farrukh – Updated 12/29/2025
What Is Quishing? QR Code Phishing Scam Explained
One of the fastest-growing cyber threats today is quishing, also known as QR code phishing. According to the 2025 Cybersecurity
Idrees Shafiq – Updated 12/10/2025
Cloud Security
Secure your cloud infrastructure with expert tips, tools, and best practices for data protection.
Data Breach
Unauthorized access exposing sensitive data, risking privacy and security.
Privacy
Protect your personal data with privacy guides, VPN reviews, and anonymity tools.
Network Security
Essential strategies to secure networks from cyberattacks and unauthorized intrusions.
Cyber Threats
How to Remove Yahoo Search from Chrome
You didn’t change anything. You didn’t ask for this. And yet, here it is, redirecting you every single time. This
Arsalan Rathore – Updated 03/10/2026
What Is a Botnet? Understanding Botnet Attacks and DDOS threats
Introduction Botnets quietly infect thousands or even millions of devices, turning them into remote-controlled weapons that can launch devastating attacks.
Bisma Farrukh – Updated 12/29/2025
What is Clone Phishing? How It Works & How to Stay Safe
Unlike generic phishing attempts that are easy to spot, clone phishing uses legitimate messages that victims trust, making it one
Bisma Farrukh – Updated 12/02/2025
VPN
How to Use a VPN on iPhone: A Comprehensive Guide
A Virtual Private Network (VPN) offers a robust solution by encrypting your internet connection, masking your IP address, and ensuring secure browsing. This guide provides a step-by-step process for setting
News

SaaS & Online Security Best Black Friday Deals 2025
This year, the event falls on November 29th, 2025, and we’ve compiled the best Black Friday SaaS and online security … Read more
Arsalan Rathore – Updated 11/11/2025

New Man-in-the-Prompt Attack Puts Generative AI Tools at Risk
This technique, named Man-in-the-Prompt, takes advantage of how AI tools interact with the browser environment, opening the door to covert … Read more
Arsalan Rathore – Updated 08/01/2025
Claroty Report Exposes Critical Security Flaws in Building Management Systems
These vulnerabilities include those already exploited in ransomware campaigns and poorly secured internet-facing systems. While BMS and BAS platforms are … Read more
Bisma Farrukh – Updated 06/26/2025