This malicious software can lock you out of your files or entire systems, demanding payment to restore access. Let’s explore what this type of malware is, how it works, and how to protect yourself.
What Is a Ransomware Attack?
A ransomware attack is a type of cyberattack in which malicious software is used to encrypt or lock a victim’s files or systems, making them inaccessible. The attacker then demands payment to restore access.
- Often spread through phishing emails, malicious attachments, compromised websites, or software vulnerabilities.
- Once executed, ransomware encrypts files or entire systems.
- Victims receive a message with instructions on how to pay the ransom, often with threats of data destruction or public exposure if they don’t comply.
- Usually demanded in Bitcoin or another cryptocurrency to avoid tracing.
How Does This Malware Work?
- Ransomware enters the system through phishing emails, malicious links, infected attachments, or unpatched software vulnerabilities. The malware silently installs itself, often disabling security tools and hiding from detection.
- It scans for valuable files and encrypts them using strong encryption algorithms or locks the entire system to prevent access.
- A ransom note appears, demanding payment (usually in cryptocurrency) for a decryption key or system access.
- Some ransomware connects to the attacker’s command-and-control server to send data or receive further instructions.
- If the ransom is paid, the attacker may send a decryption key, but there’s no guarantee that the files will be restored.
How Does It Spread?
It spreads through the following ways:
- Victims are tricked into clicking malicious links or opening infected attachments (e.g., Word or PDF files).
- Clicking on fake ads or compromised websites can trigger automatic ransomware downloads (drive-by downloads).
- Hackers exploit weak or stolen RDP credentials to access systems and manually deploy ransomware.
- Unpatched or outdated software (e.g., operating systems, browsers, plugins) can be exploited to silently install ransomware.
- Installing pirated or fake software bundled with ransomware can compromise the system.
- Ransomware can spread through infected USB sticks or external drives when plugged into a system.
- Once inside a network, ransomware can move laterally across systems, infecting shared folders and connected devices.
- Ransomware can spread through trusted software updates or third-party service providers (e.g., the Kaseya attack in 2021).
How to Detect Ransomware
Detection identifies and responds to this type of attack before it can cause significant harm. As it continues to evolve and target organizations of all sizes, effective detection methods are critical to minimize damage, avoid data loss, and prevent financial and reputational consequences.
Signature-Based Detection
- One of the oldest and most widely used techniques for ransomware detection is signature-based detection.
- This method identifies known malicious code by comparing files and processes to a database of malware signatures.
- While signature-based tools are effective at detecting established ransomware strains, they are less capable of identifying new, modified, or obfuscated versions of ransomware.
- As attackers constantly change their tactics, relying solely on this method is insufficient.
Behavior-Based Detection
- Behavior-based detection offers a more proactive approach by monitoring systems for suspicious activity patterns commonly associated with ransomware.
- These include rapid file encryption, mass file renaming or deletion, and unusual system resource usage.
- Unlike signature-based detection, this method can identify unknown ransomware variants based on their behavior rather than their appearance. However, behavior-based detection may occasionally trigger false positives, especially if legitimate software behaves similarly.
Heuristic Analysis
- Heuristic analysis aims to detect ransomware by analyzing the characteristics and actions of software code.
- This method assesses a program’s behavior and makes judgments based on pre-defined rules and logic. For example, if a file attempts to modify or encrypt a large number of documents in a short time, it might be flagged as suspicious.
- Heuristic detection helps catch previously unseen threats, though its accuracy depends on the rules defined by security analysts and can vary between tools.
AI and Machine Learning-Based Detection
- Modern cybersecurity solutions increasingly rely on artificial intelligence and machine learning to detect ransomware.
- These systems analyze vast amounts of data to learn what normal system behavior looks like and can identify subtle deviations that may indicate an attack.
- Machine learning models continuously improve, adapting to new threats as they emerge. Although these methods offer high accuracy and adaptability, they require robust datasets and careful training to avoid false alerts.
Honeypots and File Canaries
- Another effective ransomware detection strategy involves the use of honeypots and file canaries. Honeypots are decoy systems or files placed strategically to lure attackers.
- When ransomware interacts with these decoys, it alerts the system administrators. Similarly, file canaries are fake files placed in sensitive areas; any attempt to access or encrypt these files can trigger a warning.
- These techniques are beneficial for early detection but must be implemented carefully to avoid being bypassed.
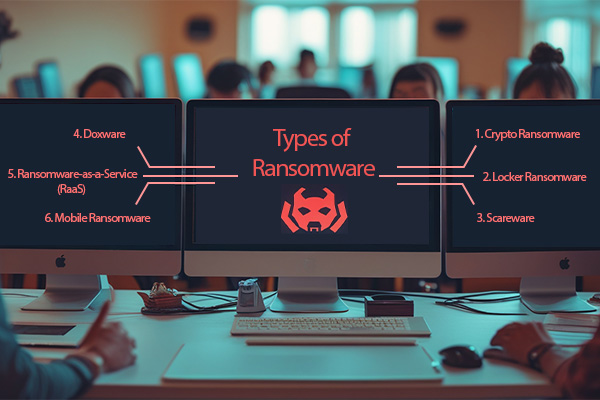
Types of Ransomware
The following types of Ransomware are common:
1. Crypto Ransomware
Crypto ransomware is one of the most common and dangerous types of ransomware. It encrypts the victim’s personal or organizational files using strong encryption algorithms, making them inaccessible without a decryption key.
The malware targets essential files such as documents, photos, and databases. After encryption, a ransom note demands payment in exchange for the decryption key. Notable examples include WannaCry and CryptoLocker. This malware does not affect the operating system but causes significant damage by locking critical data.
2. Locker Ransomware
Understanding this type of malware is crucial for protection.
Locker ransomware differs from crypto ransomware in that it locks the entire system or device, preventing the user from accessing anything. Instead of encrypting files, it blocks the user interface, often showing a full-screen ransom demand that cannot be closed.
Victims cannot use their keyboard, mouse, or any applications. However, locker ransomware typically avoids targeting core system files to ensure the system remains operational enough to receive the ransom. Examples include WinLocker and some early variants of Reveton.
3. Scareware
Scareware uses fake alerts and alarming messages to trick users into thinking their computer is infected with viruses or illegal content. It demands payment for a supposed antivirus program or cleanup tool.
While some scareware is annoying and doesn’t encrypt files, other forms may evolve into ransomware. This type often uses pop-ups and system messages to frighten users into quick action. Though less destructive than other types, scareware can still lead to financial loss and pave the way for more serious threats.
4. Doxware
Doxware, or leakware, threatens to publish or leak the victim’s sensitive or personal data if the ransom is not paid. It combines file encryption threats with public exposure, putting pressure on victims, especially businesses or public figures, to comply with the ransom demand.
This method is particularly effective because it leverages the fear of reputational damage, lawsuits, or regulatory penalties. It is a common tactic in modern double extortion attacks.
5. Ransomware-as-a-Service (RaaS)
Ransomware-as-a-Service (RaaS) is a growing business model in cybercrime. In this model, developers create and sell ransomware tools to other criminals who use them to launch attacks. The developers typically take a percentage of the ransom collected.
RaaS makes ransomware accessible even to those with little technical expertise, leading to a sharp increase in ransomware attacks globally. Popular RaaS platforms include REvil, DarkSide, and LockBit.
6. Mobile Ransomware
Mobile ransomware targets smartphones and tablets, particularly Android devices. It can lock the screen or encrypt files stored on the device, just like on a PC. Victims often receive a ransom message claiming illegal activity was detected or threatening to expose personal data.
Mobile ransomware is typically distributed through malicious apps, fake updates, or phishing links sent via SMS or messaging. This ransomware becomes more common as mobile devices become more central to daily life and business.
Real-World Ransomware Examples
These are a few of the latest real-world ransomware examples, as stated below.
Medibank (Australia, November 2022)
In November 2022, Medibank, Australia’s largest health insurer, was hit by a ransomware affiliate believed to be linked to REvil. The attackers exfiltrated personal and medical data of approximately 9.7 million customers and demanded a ransom of about $10 million. Medibank declined to pay, leading to the full data leak of 6 GB of sensitive files on the dark web.
Toyota Supply Chain Attack via Denso (March 2022)
In early 2022, a ransomware infiltration of Denso Automotive Deutschland, a key Toyota supplier, disrupted operations at 14 facilities across Japan, temporarily halting up to one-third of global Toyota production. The Pandora ransomware group claimed responsibility and threatened to leak trade secrets. While resolved within a day, the incident highlighted vulnerabilities in automotive supply chains.
Change Healthcare (United States, February 2024)
In February 2024, Change Healthcare, owned by UnitedHealth Group, suffered a massive ransomware attack that crippled pharmacy and billing systems nationwide. The incident exposed the personal data of 190 million individuals. The fallout was so severe that the U.S. Department of Health and Human Services declared a state of emergency. Response and system recovery costs totaled $3.1 billion, marking it as one of the most expensive cyberattacks in healthcare.
Ascension Health (United States, May 2024)
Ascension, one of the U.S.’s largest healthcare systems, was impacted by ransomware traced to the Black Basta gang. The attack took critical systems offline, including electronic medical records and telephony, forcing staff to use manual procedures and divert patients to alternate facilities. Investigations revealed that personal and medical data for about 5.6 million people, including insurance, SSNs, and addresses, were compromised.
Blue Yonder and Starbucks Supply Chain Disruption (November 2024)
In late 2024, Blue Yonder, a supply chain management provider, was struck by ransomware that disrupted inventory systems for major retailers including Starbucks, Morrisons, and Sainsbury’s. Retail locations experienced inventory shortages, empty shelves, and significant delivery delays. This attack underscored the rising threat of supply‑chain‑targeted ransomware.
Qilin Gang Attack on London Hospitals (United Kingdom, June 2024)
The Russian-linked Qilin ransomware group targeted Synnovis, an NHS pathology lab serving multiple hospital trusts. The attack disrupted lab operations, causing cancellations and delays in critical services like blood transfusions. Former UK cybersecurity officials described the incident as having a “major impact” and “critical,” severely impairing healthcare services across south London.
Alder Hey Children’s Hospital Data Leak (Liverpool, November 2024)
INC Ransom claimed responsibility for breaching Alder Hey Children’s Hospital, publishing patient records and financial data screenshots. Though the hospital asserted that patient care services were not disrupted, authorities are working to verify the authenticity and impact of the data leak. NHS partners coordinate with law enforcement to secure systems and assess the breach.
Medusa Ransomware Hits Critical Infrastructure (March 2025)
By March 2025, the Medusa ransomware group had targeted more than 300 organizations in healthcare, education, manufacturing, and insurance sectors. These attacks typically involved phishing or exploiting software vulnerabilities, combined with double‑extortion tactics that encrypt files and threaten data leakage if ransoms aren’t paid. The FBI and CISA issued a joint advisory highlighting the severity and scope of these campaigns.
DragonForce Targets Saudi Organizations (February 2025)
The DragonForce ransomware affiliate orchestrated attacks on real estate and construction firms in Saudi Arabia just before Ramadan. After the ransom deadline, the group published about 6 TB of stolen data on a separate leak site. This highly strategic timing demonstrates how ransomware actors combine cultural, financial, and reputational pressure in double extortion schemes.
Morpheus & Gd‑Lockersec (January 2025)
New ransomware-as-a-service (RaaS) groups appeared in early 2025. Morpheus began publicly claiming victims in January. Gd-Lockersec launched with specific “rules” (e.g., not targeting non-profit hospitals or companies in certain countries), signifying the growing complexity and self-regulation within criminal ransomware networks. Victim counts were small but rapidly growing.
How to Protect Against This Type of Malware?
Protecting against this type of malware involves a combination of preventive measures, user awareness, and system defenses.
1. Keep Software and Systems Updated
One of the most effective ways to prevent ransomware attacks is to keep all software, operating systems, and applications up to date. Cybercriminals often exploit known vulnerabilities in outdated systems to gain access. Regularly applying security patches and updates ensures these gaps are closed before being exploited.
2. Use Strong Antivirus and Endpoint Protection
Installing reputable antivirus and endpoint protection software helps detect and block ransomware before it can execute. Modern security solutions use behavior-based detection to identify suspicious activity, such as rapid file encryption or unauthorized access, and can stop ransomware in real time. These tools should also include a firewall, email filtering, and web protection features.
3. Backup Data Regularly
Frequent and secure backups are critical in minimizing damage from a ransomware attack. Backups should be stored offline or in a safe, immutable cloud environment to prevent them from being encrypted by ransomware. Testing backups regularly is essential to ensure they can be restored quickly.
4. Enable Multi-Factor Authentication (MFA)
Multi-factor authentication adds an extra layer of security by requiring more than just a password to access accounts or systems. This is particularly important for remote desktop access, admin accounts, and sensitive systems. Even if passwords are stolen or guessed, MFA can prevent unauthorized access.
5. Educate Users and Employees
Human error remains one of the leading causes of ransomware infections. Conduct regular cybersecurity training for employees and users to help them recognize phishing emails, suspicious links, and unsafe websites. Awareness reduces the chances of accidentally triggering ransomware through social engineering.
6. Restrict User Access and Permissions
Use the principle of least privilege (PoLP) to limit access to files and systems. Users should only have access to the data and tools necessary for their role. Admin privileges should be tightly controlled, as ransomware often uses these to spread across networks and encrypt broader sets of files.
7. Disable Macros and Remote Desktop Protocol (RDP) When Not Needed
Macros in Microsoft Office documents are a standard delivery method for ransomware. Disable macros by default unless necessary. Similarly, if Remote Desktop Protocol is not required, it should be disabled or restricted to prevent external access by attackers.
8. Monitor and Respond to Threats
Monitor network activity using tools like Security Information and Event Management (SIEM) systems or Endpoint Detection and Response (EDR) platforms. These tools can alert administrators to suspicious behavior and allow for a rapid response before ransomware spreads.
9. Segment the Network
Network segmentation divides your systems into isolated sections, making it harder for ransomware to spread across the entire organization. If one segment is compromised, others can remain safe, limiting the scope of the damage.
10. Develop and Test an Incident Response Plan
Prepare for the possibility of a ransomware incident by creating a detailed response plan. This plan should include roles, communication strategies, and technical steps for containment and recovery. Regular testing ensures the plan is effective and everyone knows their responsibilities during an emergency.
Conclusion
This malware is one of the most dangerous cybersecurity threats today. The best defense includes a mix of proactive detection, employee awareness, regular backups, and robust patch management. Whether you’re an individual or an enterprise, staying informed and prepared is your best shield against this growing menace.
FAQs
Who is at risk of a ransomware attack?
Everyone, from individuals to global enterprises. However, healthcare, education, finance, and government sectors are especially high-value targets due to the sensitivity of their data and the need for quick recovery.
How does ransomware infect a device?
Infections typically occur through:
Clicking on malicious email attachments or links
Downloading software from untrusted sources
Visiting compromised websites
Exploiting unpatched system vulnerabilities
Is ransomware a type of malware?
Yes. This type of malware is specifically designed for extortion. It locks or steals data and demands a ransom for its return.
Can ransomware affect smartphones and tablets?
Yes. While not as common as desktop infections, this type of malware targeting Android devices has increased. These attacks usually arrive via malicious apps or links. iOS is less vulnerable but not immune, especially if jailbroken.
Can law enforcement help in a ransomware attack?
Yes. Law enforcement agencies can:
Investigate and potentially track down attackers
Help recover stolen data (in rare cases)
Advise victims and assist in response coordination.
However, they typically discourage paying ransoms, as it fuels further attacks.
What is triple-extortion ransomware?
Triple-extortion adds a third layer of pressure:
Encrypts data (traditional extortion)
Steals and threatens to publish it (double extortion)
Threatens or contacts customers, partners, or media to amplify pressure
Sophisticated gangs increasingly use this tactic to maximize payouts.
How fast can ransomware encrypt a network?
In some cases, within minutes. Once executed, this type of malware can encrypt tens of thousands of files in less than an hour. Advanced versions may also disable backups and evade detection before the final encryption phase is launched.
Table of Contents
