SQL Injection allows attackers to manipulate SQL queries used by an application, potentially exposing sensitive data, bypassing login authentication, altering databases, or even taking complete control of a server. Despite being well-known for decades, SQL injection attacks remain among the top security risks due to insecure coding practices and inadequate input validation. This blog explains what SQL injection is, how it works, provides real-world examples, outlines the types of SQL injection, and offers guidance on how to prevent these attacks effectively.
What Is SQL Injection?
SQL Injection is a critical security vulnerability that allows attackers to interfere with the SQL queries an application sends to its database. By injecting malicious SQL code into input fields such as login forms, search bars, or URL parameters, attackers can manipulate the query and gain unauthorized access to data. Essentially, SQLi exploits applications that fail to sanitize and validate user input before incorporating it into SQL statements.
SQL Injection occurs when an application dynamically constructs SQL queries using unsanitized user input. When the input is not filtered correctly, attackers can directly modify the query’s logic. Vulnerable applications treat attacker-controlled input as part of the SQL command rather than as data, allowing harmful operations such as retrieving hidden information, deleting records, or altering the database structure.
SQL Injection Attack
A SQL injection attack involves deliberately inserting malicious SQL commands into a text field or query parameter. The attacker monitors how the application responds to different inputs, adjusting the payload to manipulate the underlying database. Depending on the vulnerability, SQLi attacks may allow unauthorized access to data, theft of credentials, privilege escalation, or complete database compromise.
A SQLi attack is not always immediately visible. Sometimes, the attacker may only receive subtle clues, such as error messages or timing differences, that indicate how the database responds. Skilled attackers can chain SQL injection exploits with other vulnerabilities, enabling them to execute remote commands, extract sensitive files, or pivot deeper into the network.
SQL Injection Vulnerability
A SQL injection vulnerability exists when an application constructs SQL queries using concatenated strings directly from user input. This often occurs due to insecure coding practices, outdated libraries, or a lack of parameterized queries. Vulnerable code typically resembles:
SELECT * FROM users WHERE username = ‘” + userInput + “‘”;
Such patterns allow attackers to inject arbitrary SQL code into the query. SQL injection vulnerabilities can be found in login pages, search fields, API parameters, cookies, and even hidden form fields.
SQL Injection Example
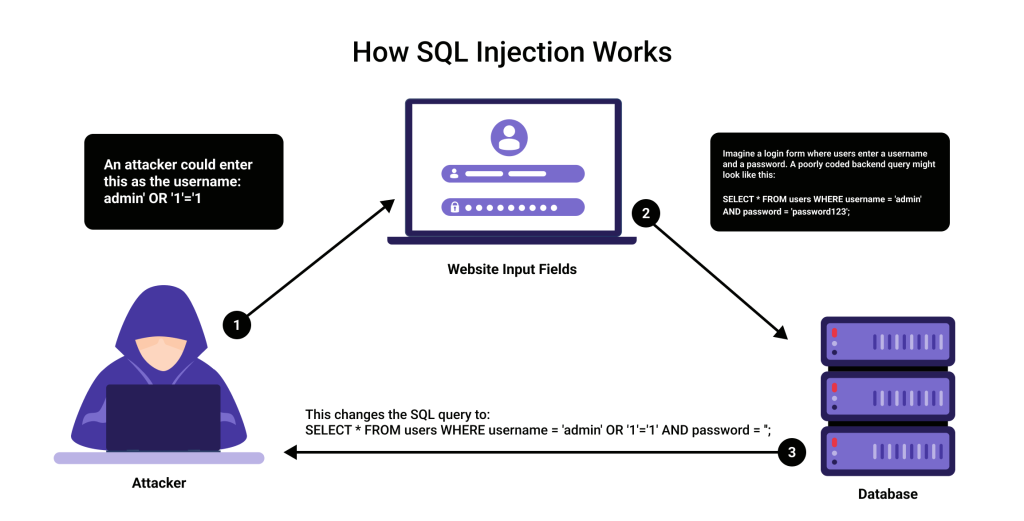
Imagine a login form where users enter a username and a password. A poorly coded backend query might look like this:
SELECT * FROM users WHERE username = ‘admin’ AND password = ‘password123’;
An attacker could enter this as the username:
admin’ OR ‘1’=’1
This changes the SQL query to:
SELECT * FROM users WHERE username = ‘admin’ OR ‘1’=’1′ AND password = ”;
Since ‘1’=’1′ is always true, the attacker bypasses authentication and logs in without knowing the actual password. This is one of the simplest yet most dangerous real-world examples of SQL injection.
How SQL Injection Works?
SQL Injection works by manipulating user input so that it becomes part of a SQL query executed by the database. When a web application does not validate or sanitize the user’s input, an attacker can inject malicious SQL code into input fields, URLs, or HTTP parameters. The database mistakenly executes the attacker’s code as if it were part of the legitimate query.
Here’s how SQL injection works:
1. Applications Dynamically Build SQL Queries Using User Input
Many applications construct SQL queries like this:
SELECT * FROM users WHERE username = ‘” + input + “‘ AND password = ‘” + input2 + “‘;
If the input is not sanitized, the application inserts the user’s input directly into the query.
2. Attackers Insert Malicious SQL Instead of Normal Input
Example input:
‘ OR ‘1’=’1
Because the app does not treat input as data, the injected SQL becomes part of the command.
This turns the original query into:
SELECT * FROM users WHERE username = ” OR ‘1’=’1′ AND password = ”;
Since ‘1’=’1′ is always true, the query returns all users, allowing for login bypass.
3. The Database Executes the Malicious Query
SQL databases do not distinguish between legitimate and malicious parts of a query. They simply execute the final combined SQL statement.
Depending on the database permissions, an attacker may be able to:
- Retrieve confidential data
- Modify or delete records.
- Bypass authentication
- Add a new admin accounts
- Execute system commands
- Take complete control of the server.
4. Attackers Use the Application’s Responses to Fine-Tune the Attack
Even small clues help attackers refine their payloads:
- Error messages → reveal database structure
- Timing delays → used in blind SQL injection
- Changes in page content → indicate true/false results.
Over time, this allows attackers to extract large amounts of data or escalate their access.
5. Exploitation Varies by SQL Injection Type
Different SQLi methods work in different ways:
- Error-based SQLi → forces database errors to reveal details
- Union-based SQLi → merges attacker queries with legitimate output
- Blind SQLi → infers information by observing application behavior
- Stored SQLi → malicious input is stored and executed later.
6. Poor Input Validation Is the Root Cause
SQL Injection happens almost entirely because user input is not:
- sanitized
- validated
- parameterized
When developers concatenate user input directly into SQL statements, they give attackers a direct entry point to the database.
Key SQL Injection Statistics and Data
- SQL injection vulnerabilities remain one of the oldest yet most actively exploited security weaknesses, first discovered in 1998.
- SQL Injection makes up 6.7% of vulnerabilities found in open-source projects.
- SQL Injection accounts for around 10% of vulnerabilities found in closed-source/commercial software.
- Open-source ecosystems had recorded over 2,400 SQL injection CVEs by 2024, with the number continuing to rise each year.
- More than 20% of organizations scanned for the first time are found to have at least one SQL injection vulnerability.
- Vulnerable applications typically have an average of 30 separate SQL injection entry points.
- SQL injection was responsible for 65.1% of all web application attacks in a multi-year global study (2017–2019).
- Around 42% of attacks on public-facing systems are attributed to SQL injection.
SQL Injection Types
The following are the basic types of SQL injection:
1. Error-Based SQL Injection
Error-based SQLi relies on database error messages to reveal information. When an attacker injects payloads that cause database errors, the system may return detailed messages that expose database structure, table names, or configuration details. These insights enable the attacker to craft more precise and damaging queries.
2. Union-Based SQL Injection
Union-based SQL injection (SQLi) utilizes the SQL UNION operator to combine results from multiple SELECT queries. Attackers use it to extract data from other tables by merging them into the output of a legitimate query. If successful, sensitive information such as usernames, passwords, or payment details can be displayed on the webpage.
3. Blind SQL Injection
Blind SQL injection occurs when an application does not display error messages or the results of queries. Instead, attackers infer information based on the application’s behavior, such as page responses, delays, or redirection patterns. Types of blind SQLi include Boolean-based and Time-based injection.
4. Stored (Second-Order) SQL Injection
Stored SQLi happens when malicious input is saved in the database and executed later. For example, if an attacker inserts harmful SQL code in a comment field and another part of the application retrieves that data and executes it in a query, the exploit is executed secondarily.
SQL Injection Prevention
Preventing SQL Injection requires a combination of secure coding practices, proper database configuration, input validation, and continuous security testing. While no single method is a complete solution, using multiple layers of protection significantly reduces the risk of SQL injection (SQLi) attacks.
Below are the most effective SQL injection prevention techniques.
1. Use Prepared Statements (Parameterized Queries)
Prepared statements ensure that user input is always treated as data, not as executable SQL code. The query structure is defined first, and user inputs are safely inserted later.
Why it works:
The database knows the SQL syntax separately from the user-supplied values, making SQL injection impossible.
Example (PHP PDO):
$stmt = $pdo->prepare(“SELECT * FROM users WHERE username = ? AND password = ?”);
$stmt->execute([$username, $password]);
2. Use Stored Procedures
Stored procedures move the SQL logic to the database itself. When used correctly (without dynamic SQL inside), they reduce the chances of SQL injection.
Example:
EXEC GetUserDetails @username = ‘john’, @password = ‘12345’;
Stored procedures are not immune to SQL injection if developers construct SQL strings within them.
3. Apply Strong Input Validation
Applications should strictly validate user input before using it. Validation ensures users cannot submit unexpected characters or formats.
Best practices:
- Allow only expected characters (whitelisting)
- Enforce data types (integer, email, date)
- Reject unusual or dangerous characters (quotes, semicolons, operators)
4. Escape User Input
Input escaping adds special characters before user-supplied data to prevent it from being interpreted as SQL code. Escaping alone is not a complete solution; it should be used in conjunction with other methods.
5. Use the Principle of Least Privilege
Applications should connect to the database using accounts that have the minimum necessary permissions. This limits the damage even if SQL injection occurs.
For example:
- A login page should only have SELECT access
- An admin panel can have UPDATE/DELETE, but it is protected behind authentication
6. Disable Detailed Error Messages
Never show database error messages to users. These errors reveal table names, column names, and SQL syntax, allowing attackers to craft SQL injection payloads.
Safe approach:
- Show general messages to users
- Log detailed errors internally.
7. Implement a Web Application Firewall (WAF)
A WAF can block standard SQL injection payloads before they reach your application. Cloud-based WAFs (e.g., Cloudflare, AWS WAF) offer additional protection.
Modern WAFs can detect:
- SQL operators (OR, AND, UNION)
- Suspicious patterns (’, –, /* , xp_cmdshell)
- Malicious URL parameters
8. Keep Software & Frameworks Updated
Many SQL injection vulnerabilities come from outdated systems or libraries. Regular updates often include fixes for SQLi-related flaws.
Examples:
- Old PHP versions
- Outdated ORM tools
- Unpatched CMS plugins
9. Use Secure ORM Tools (Hibernate, Sequelize, Django ORM)
Object-Relational Mappers (ORMs) generate SQL queries automatically. When appropriately used, ORMs make SQL injection more complicated because they handle escaping and parameters internally. If developers bypass ORM safety features by writing raw SQL, the risk returns.
10. Conduct Regular Security Testing
Continuous testing helps identify vulnerabilities before attackers can exploit them.
Techniques include:
- Static code analysis
- Dynamic application testing (DAST)
- Penetration testing
- Automated vulnerability scanners
- Manual code reviews
Conclusion
SQL injection remains a powerful and dangerous attack method in today’s digital landscape. It exploits weak coding practices, inadequate input validation, and insecure database queries. By understanding how SQL injection works, recognizing common examples, and implementing proven prevention techniques such as parameterized queries and least-privilege access, developers can significantly reduce the risk of SQL injection vulnerabilities. Regular testing and adherence to secure coding standards are essential for preventing attackers from exploiting these weaknesses. Strengthening your application against SQL injection is not just best practice; it’s a critical necessity for protecting users, data, and business integrity.
FAQs
Here are the frequently asked questions that follow.
When was SQL injection first discovered?
SQL injection was first documented in the late 1990s and gained widespread recognition after a 1998 paper by cybersecurity researcher Jeff Forristal (also known as Rain Forest Puppy) highlighted the vulnerability.
Do attackers need physical access to perform SQL injection?
No. SQL injection attacks are usually performed remotely over the internet. Attackers only need access to a vulnerable input field or API to launch their attack.
What is error-based SQL injection?
Error-based SQL injection is a technique in which attackers utilize database error messages to extract details about the database, such as its table structure or column names.
What is union-based SQL injection?
Union-based SQL injection utilizes the SQL UNION operator to combine attacker-controlled queries with legitimate ones, enabling the disclosure of sensitive data from other database tables.
Table of Contents
